Quote of the Day
I have long been of the opinion that if work were such a splendid thing the rich would have kept more of it for themselves.
— Bruce Grocott, British politician
Introduction
One of the more common problems in the life of a digital hardware designer is to divide down a master clock to some desired lower frequency value. If life is kind, the master clock is an integer multiple of the desired clock and the problem can be solved with a simple counter. Unfortunately, life is rarely kind and the master clock frequency is usually not an integer multiple of the desired clock. In this case, the designer will need to do a little work. One common solution is to use a dual-modulus counter. This blog will work through an example that came up a while back.
What is a Dual-Modulus Counter?
The dual-modulus counter allows us to design a clock divider with a non-integer modulus, which I call M. Figure 1 illustrates the basic idea. In Figure 1, we desire a modulus that is between N and N-1. We vary the duty cycle of each counter so that the average modulus equals M. Clearly, the instantaneous frequency will never be exactly what we want. But many problems require only that the average value be exactly right and the instantaneous value is of less interest.

Figure 1: Block Diagram of a Dual-Modulus Counter.
Basic Dual-Modulus Mathematics
We can compute the modulus we desire using Equation 1.
| Eq. 1 |
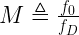 |
where M is the desired modulus, f0 is our master clock, and fD is desired output frequency from the dual-modulus divider. Of course, f0 > fD.
Let's assume that N and N-1 are integers such that N > M > N-1. N and N-1 are the moduli of our counter. We can compute the value of N (and correspondingly, N-1) as shown in Equation 2.
| Eq. 2 |
 |
As shown in Equation 3, we can restate M in terms of its integer and fractional part, where the fractional part is assumed to be expressible as an integer ratio A/C.
| Eq. 3 |
 |
where A represents the number of N-1 division operations in a cycle and C represents the total number of division cycles (both N and N-1).
| Eq. 4 |
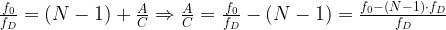 |
Ease of implementation requires that we make sure that A and C are relatively prime (i.e. no common factors). Equation 5 shows how to compute both A and C.
Given these equations, we can generate a high-level design for our dual-modulus counter.
One Thing to Note
The dual-modulus counter will divide the master clock by N and N-1. One could do all the divide-by-N operations and then all the divide-by-(N-1) operations. While correct, the generated output clock can have some rather large phase variations from an ideal output frequency. These phase deviations can be minimized by evenly mixing the N and N-1 divisions.
There are various ways to spread the divisions out. I will not dwell on these approaches here, but in the Worked Example below I do illustrate one approach in my Mathcad model.
Worked Example
Computing the Constants
We had a problem a while ago where we needed to generate a 2.048 MHz clock from a 78.125 MHz clock. I threw this example into Mathcad and the results are shown in Figure 2.

Figure 2: Dual-Modulus Worked Example.
Spreading the Different Divisions Out
One can use the modulo operation to spread the different divisions out. Figure 3 illustrates the approach. The vector m in Figure 3 has entries equal to their count values (i.e. 0 to 2047), which means each entry corresponds to a division. I divide by 39 for every entry where the index mod (2048/301) passes through 0 and I divide by 38 for all other entries. The quotient of 2048/301 is the total number of division cycles divided by the number of divide-by-39 cycles. This spreads the divisions out evenly.

Figure 3: Evenly Spreading Out the Divisions.
Conclusion
This blog post shows how to design a basic dual-modulus counter. It presents both the theory and a worked example. This example is very similar to a frequency divider that is currently out in the field inside thousands of units.
For an example of a dual modulus counter design that everyone is familiar with, see this post on the Gregorian calendar.
Save
Save
Save